VMware NSX
What is VMware NSX?
VMware NSX is a virtual networking and security software product family created from VMware's vCloud Networking and Security (vCNS) and Nicira's Network Virtualization Platform (NVP) intellectual property.
NSX software-defined networking, or SDN, is part of VMware's software-defined data center, or SDDC, concept, which offers cloud computing on VMware virtualization technologies. The company's stated goal with NSX is to provision virtual networking environments without a command-line interface (CLI) or other direct administrator intervention.
Network virtualization abstracts network operations from the underlying hardware onto a distributed virtualization layer, much like server virtualization does for processing power and operating systems (OSes). VMware vCNS virtualizes Layers 4-7 of the Open Systems Interconnection model. Nicira's NVP virtualizes the network fabric, Layer 2 and Layer 3.
NSX exposes logical firewalls, switches, routers, ports and other networking elements to enable virtual networking among vendor-agnostic hypervisors, cloud management systems and associated network hardware. It also supports external networking and security ecosystem services.
Important features of NSX
NSX comes with a range of features, including the following:
- Switching. NSX virtual switches use unique Virtual Extensible LAN (VXLAN) network identifiers to create a logical overlay extension for the L2 network. Applications and tenant virtual machines (VMs) can then be logically wired to this extension. These logical broadcast domains enable greater flexibility and faster deployment, while providing the characteristics of a virtual local area network (VLAN) without the risk of sprawl.
- Routing. NSX performs routing with both logical distributed routers, which create routes between virtual networks at the hypervisor kernel, and physical routers for scale-out routing with active-active failover.
- Distributed firewalling. The NSX distributed firewall is a hypervisor kernel-embedded firewall that spreads over the VMware ESXi A network administrator can create custom firewall policies that are enforced at the virtual network interface card level. This approach ensures stateful firewall services for VMs and increases visibility and control for virtualized networks and workloads.
- Load balancing. NSX's L4-L7 load balancer intercepts, translates and manipulates network traffic to improve enterprise application availability and scalability. The NSX load balancer includes support for Secure Sockets Layer offload for pass-through and server health checks. The L4 load balancer offers packet-based load balancing that sends the packet to a specific server after it's manipulated. The L7 load balancer offers socket-based load balancing that establishes client- and server-facing connections for a single request.
- Virtual private network (VPN). NSX includes site-to-site and remote access VPN capabilities and unmanaged VPN for cloud gateway services.
- NSX Edge gateway. The NSX Edge gateway is a VM that behaves like an appliance to provide L3 routing, firewall, site-to-site VPN, load balancing and other capabilities. This feature also offers support for VXLAN-to-VLAN bridging for seamless connection to physical workloads.
- Application programming interface (API). NSX uses a representational state transfer-based API to simplify third-party product and service integration and to integrate NSX with cloud management for additional automation capabilities.
- Operations. Native operations capabilities include Central CLI, Switch Port Analyzer, IP Flow Information Export, Application Rule Manager, Endpoint Monitoring and integration with VMware vRealize Suite for proactive monitoring, analytics and troubleshooting.
- Dynamic security policy. NSX Service Composer enables the network administrator to provision and assign network and security services to applications. The administrator also can use Service Composer to create dynamic security groups with custom filters, such as VMware vCenter objects and tags, OS type and Active Directory
- Cloud management. NSX natively integrates with vRealize Automation and OpenStack for cloud management.
- Cross-vCenter Networking and Security (Cross-VC NSX). This capability scales NSX vSphere across vCenter and data center boundaries. Network administrators can use it to address capacity pooling across vCenters, simplify data center migration, and perform long-distance vMotions and disaster recovery (DR).
- Log management. NSX integrates with vRealize Log Insight, which receives log entries from ESXi hosts, uses content packs to process the information each log entry contains and identifies issues within the NSX deployment.
NSX use cases
Microsegmentation, IT automation and DR are three common applications for VMware NSX adoption. These uses aim to resolve issues associated with network virtualization, such as poor traffic performance and security gaps. Here's how they work:
- Microsegmentation takes the common networking practice of segmentation and applies it at a granular level to address network security. This enables the network administrator to establish a zero-trust security perimeter around a set of resources, such as workloads and network segments. Admins can also add east-west firewall functionality to the data center using microsegmentation. NSX also enables the administrator to create security policies for specific workloads, regardless of where they sit in the network topology.
- Data center automation enables fast and flexible network provisioning. The network administrator can rapidly create a new network or network segment with workloads, resources and security policies already attached to it. This eliminates bottlenecks and makes NSX ideal for application testing and working with erratic workloads, which NSX can keep logically isolated on the same physical network.
- Disaster recovery also relies on automation. NSX integrates with orchestration tools, such as vSphere Site Recovery Manager (SRM), which automates failover and DR. When paired with NSX, SRM is used for storage replication and to manage and test recovery plans. SRM also integrates with Cross-VC NSX. Introduced in NSX 6.2, Cross-VC NSX enables logical networking and security across multiple vCenters, which makes it easier to enforce consistent security policies without the need for manual intervention. When used in conjunction with Cross-VC NSX, SRM automatically maps universal networks across protected and recovery sites.
Other ways that VMware NSX is used include the following:
- Multi-cloud networking. Users manage security and networking policies in public and private clouds across a single pane of glass for applications running on VMs, in containers and on bare metal.
- Network automation. Users automate network function and security operations that hardware-based appliances previously handled.
- Container networking and management. NSX provides global visibility across containers that helps with troubleshooting traffic issues and security dependencies.
- Accelerated application delivery. Users automate network and security service provisioning, which speeds application and infrastructure-as-code delivery.
- Advanced load balancing. VMware highlights the ability of VMware Solution Exchange to transform hybrid and hardware load-balancing implementations into software-defined implementations.
NSX licensing and versions
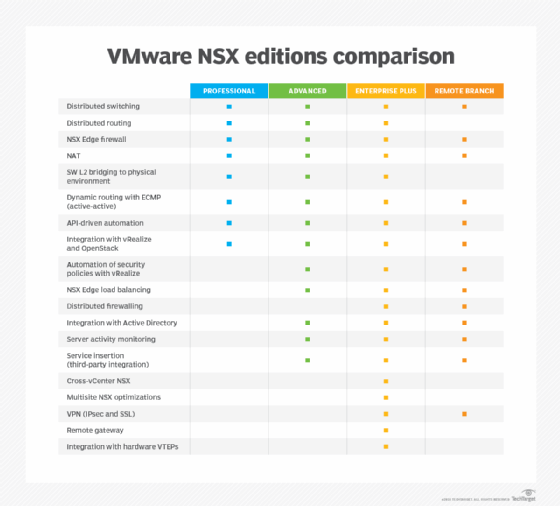
VMWare offers the following four licensing editions for NSX:
- Professional
- Advanced
- Enterprise Plus
- Remote and Branch Offices (ROBO)
The NSX Professional edition is for organizations that require network agility and automation, according to VMware. It includes features such as distributed switching and routing, as well as integration with vRealize Suite and OpenStack.
NSX Advanced is a midrange edition that offers the same capabilities as the Professional license, as well as microsegmentation for a more secure data center. It also has features such as NSX Edge load balancing and distributed firewalling.
The highest tier is NSX Enterprise Plus, which has the same capabilities as the Advanced license, plus networking and security across multiple domains with features such as Cross-VC NSX.
The ROBO edition is offered on a per-VM basis, as opposed to per-host. It includes most of the features of the Advanced tier.
In addition to these NSX licenses, VMware customers can buy NSX-T and NSX Cloud. NSX-T was released in February 2017. It offers networking and security management for non-vSphere application frameworks, multiple Kernel-based VM distributions and OpenStack environments. NSX-T also supports Photon Platform, VMware's cloud-native infrastructure software for containers.
NSX Cloud takes NSX-T components and integrates them with the public cloud. NSX Cloud customers have access to a multi-tenant dashboard, which is integrated with VMware Cloud Services. It can develop and test applications with the same network and security profiles used in the production environment.
NSX offers additional distributed security features with NSX add-on licenses.
Certification and training
VMware offers four certifications for NSX:
- VMware Certified Technical Associate-Network Virtualization (NV). VMware's entry-level NSX certification tests a candidate's ability to identify use cases for the NSX platform, understand NSX terminology and navigate the platform's user interface.
- VMware Certified Professional-NV. VMware's professional-level NSX certification demonstrates a candidate's ability to install, configure and administer NSX virtual networking implementations.
- VMware Certified Advanced Professional (VCAP)-NV. VMware's advanced professional NSX certification checks a candidate's ability to deploy an NSX-based data center networking infrastructure. The advanced professional certification has two versions:
- VCAP-NV Deploy. Tests that candidates can deploy and optimize NSX networks to provide a reliable, scalable virtualized network.
- VCAP-NV Design. Candidates must demonstrate the ability to gather customer information, including constraints, risk, requirements and assumptions. They then use the information to make design recommendations for NSX-T Data Center implementations.
- VMware Certified Design Expert-NV. This is the highest-level NSX certification, where candidates demonstrate their familiarity with vSphere and NSX and the ability to design an NSX-based data center networking infrastructure.
VMware provides resources for NSX certification training, including instructor-led courses, self-paced courses, cloud-based lab environments and learning subscriptions. NSX certification candidates can take an online practice exam and join study groups.
NSX enables users to deploy VMs. Learn how to deploy VMs with this free template.